Web Development
Unlock your web development potential by mastering React, build dynamic websites, and launch your tech career today.
 3 months
3 months 11 modules
11 modulesMachine Learning
Harness the power of algorithms, unlock data insights, and shape the innovations with Machine Learning Program.
 3 months
3 months 9 modules
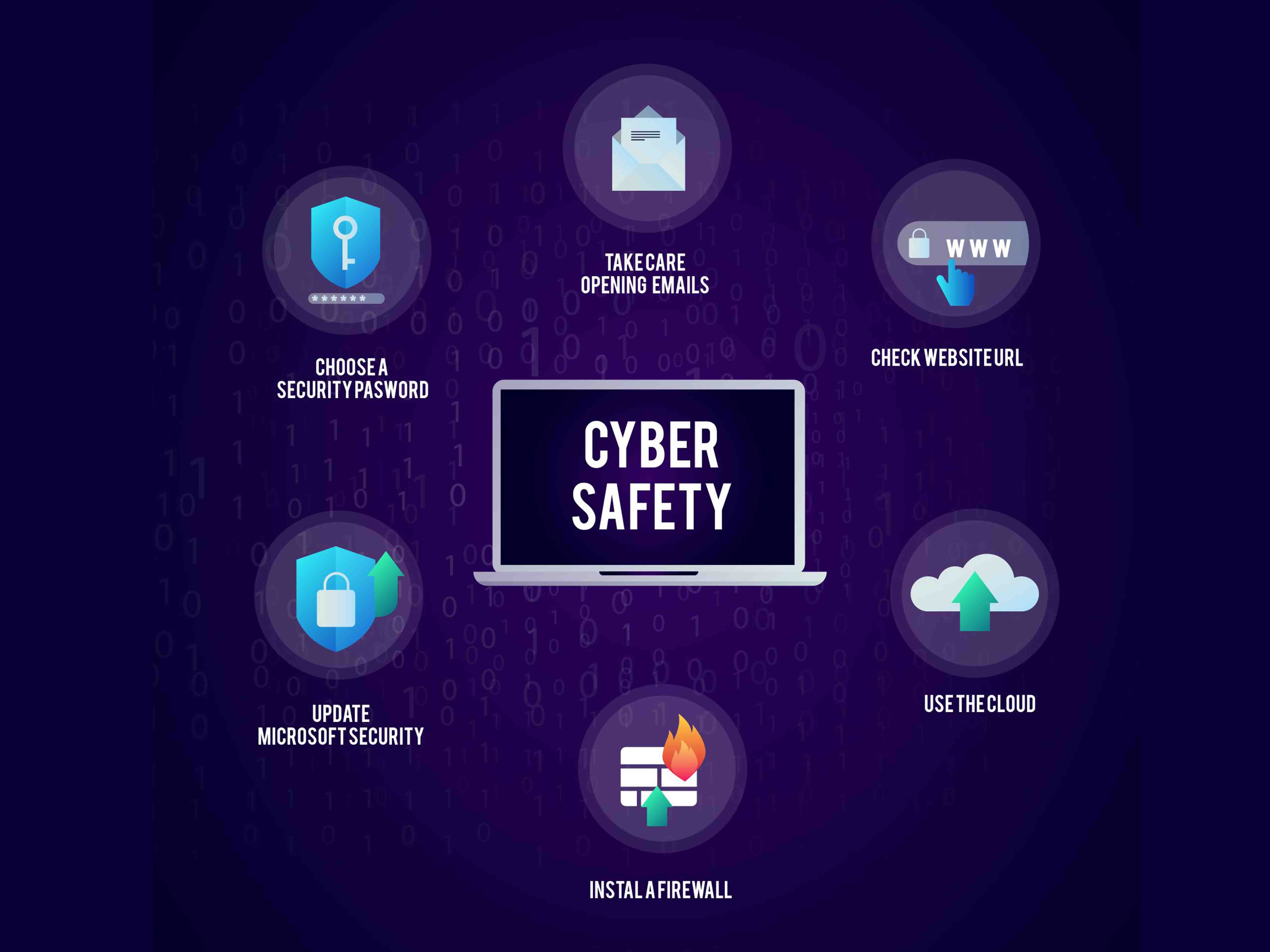
9 modulesCyber Security
Build a strong foundation for Digital Safety by mastering Cyber Security
 3 months
3 months 9 modules
9 modulesArtificial Intelligence
Master the fundamentals and cutting-edge applications through our comprehensive course designed for aspiring AI enthusiasts.
 3 months
3 months 6 modules
6 modulesPython
Explore Python language's versatility and learn to code efficiently
 3 months
3 months 25 modules
25 modulesData Science
Learn to decode patterns, predict trends, crunch data through the comprehensive course on Data Science.
 3 months
3 months 13 modules
13 modulesApp Development
Build your skillset for app development by covering from concept to code.
 3 months
3 months 10 modules
10 modulesData Structures
Become placement ready for MAANG companies by mastering Data Structures and Algorithms
 3 months
3 months 13 modules
13 modulesJAVA
Skill up by learning from fundamental to advanced applications of Java.
 3 months
3 months 8 modules
8 modulesDigital Marketing
Get ready for marketing in the digital age & strategize for the Modern Businesses.
 3 months
3 months 22 modules
22 modulesHR
Learn the science of human resources management to elevate the efficiency of the organization.
 3 months
3 months 17 modules
17 modulesFinance
Understand the ways to strategize for the financial fitness of the organization.
 3 months
3 months 16 modules
16 modulesIoT & Robotics
Learn the science behind the integration of the physical & virtual world through IoT and Robotics.
 3 months
3 months 8 modules
8 modulesEmbedded System
Gain the knowledge to design & build smart devices for tomorrow.
 3 months
3 months 7 modules
7 modules